Introduction
As organisations continue to evolve in a digital-first world, secure internet access and traffic management are crucial for maintaining productivity and protecting sensitive data. Microsoft Entra Global Secure Access (GSA) provides a robust solution for controlling and monitoring web traffic while ensuring secure access to Software-as-a-Service (SaaS) applications.
This guide will walk you through the steps of implementing Microsoft Entra Global Secure Access (GSA), explain the licensing requirements, and clarify the key differences between GSA and Security Service Edge (SSE) solutions, helping you make informed decisions on your network security strategy.
What is Global Secure Access (GSA)?
Microsoft Entra Global Secure Access (GSA) is a comprehensive, cloud-native solution designed to enhance security and control over internet traffic for users across any network or device. Integrated with Microsoft’s ecosystem, GSA enables secure, direct connections to Microsoft services while providing administrators with granular control over web content and traffic.
Key features include:
- Secure Web Gateway (SWG) capabilities to monitor and control web traffic.
- Web content filtering to ensure that access to specific sites and applications is either restricted or allowed.
- Internet traffic management that ensures secure access to SaaS applications and web resources.
By deploying GSA, organisations can effectively safeguard user access to the internet, improve productivity, and enhance user experience while ensuring security compliance.
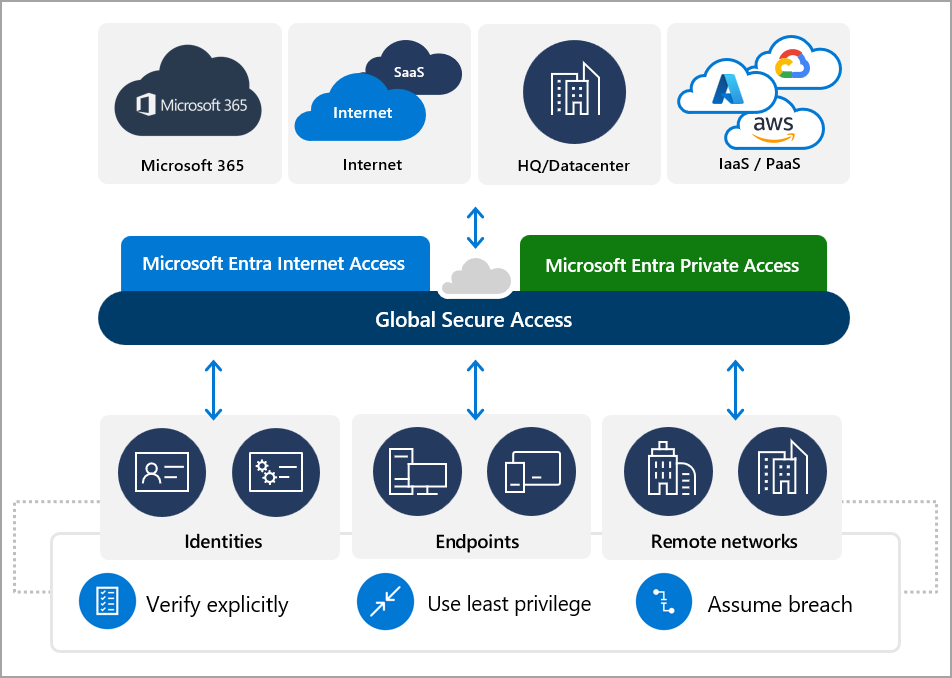
What is Security Service Edge (SSE)?
Security Service Edge (SSE) is a broader cybersecurity solution designed to address the needs of secure internet access in modern organisations. SSE solutions, which include cloud-delivered services such as Secure Web Gateways (SWG), Cloud Access Security Brokers (CASBs), and Zero Trust Network Access (ZTNA), provide an integrated approach to protect data and users regardless of location.
SSE is part of the broader Secure Access Service Edge (SASE) framework, which combines both network and security functionalities. It primarily focuses on securing internet access and traffic without the need for traditional security appliances like firewalls, providing real-time protection.
Key SSE features include:
- Web and cloud traffic security using SWG and CASB solutions.
- Zero Trust architecture for secure, identity-based access.
- Data loss prevention to monitor and restrict sensitive information sharing.
SSE solutions focus on securing a wide range of internet traffic, from accessing corporate applications to managing data and user access across various endpoints.
The Difference Between GSA and SSE
While both GSA and SSE solutions are designed to secure internet traffic, there are key differences between them:
- Scope:
- GSA is primarily focused on providing direct secure access to Microsoft services, leveraging Microsoft Entra ID for seamless integration. It is particularly beneficial for organisations heavily embedded in the Microsoft ecosystem, providing more control over SaaS application traffic.
- SSE, on the other hand, is a broader solution that secures all types of internet traffic, including cloud applications, SaaS platforms, and data access, regardless of the platform used.
- Integration:
- GSA integrates directly with Microsoft Entra ID, providing enhanced visibility and control over Microsoft services.
- SSE works with a wider range of third-party services and tools, offering flexibility for multi-cloud and hybrid environments.
- Target Audience:
- GSA is ideal for organisations that use Microsoft 365 and other Microsoft services extensively and need a solution that integrates seamlessly with their existing infrastructure.
- SSE is more suited for organisations with a broader range of services, requiring a comprehensive security solution for diverse applications and devices.
Step-by-Step Guide to Implementing Global Secure Access (GSA)
Follow these steps to set up Microsoft Entra Global Secure Access (GSA) with Internet Access and ensure seamless integration with your organisation’s security policies.
Step 1: Log into the Microsoft Entra portal
- Visit the Microsoft Entra portal and log in using your administrator credentials.
Step 2: Navigate to the GSA section
- In the left-hand menu, select Global Secure Access under Security.
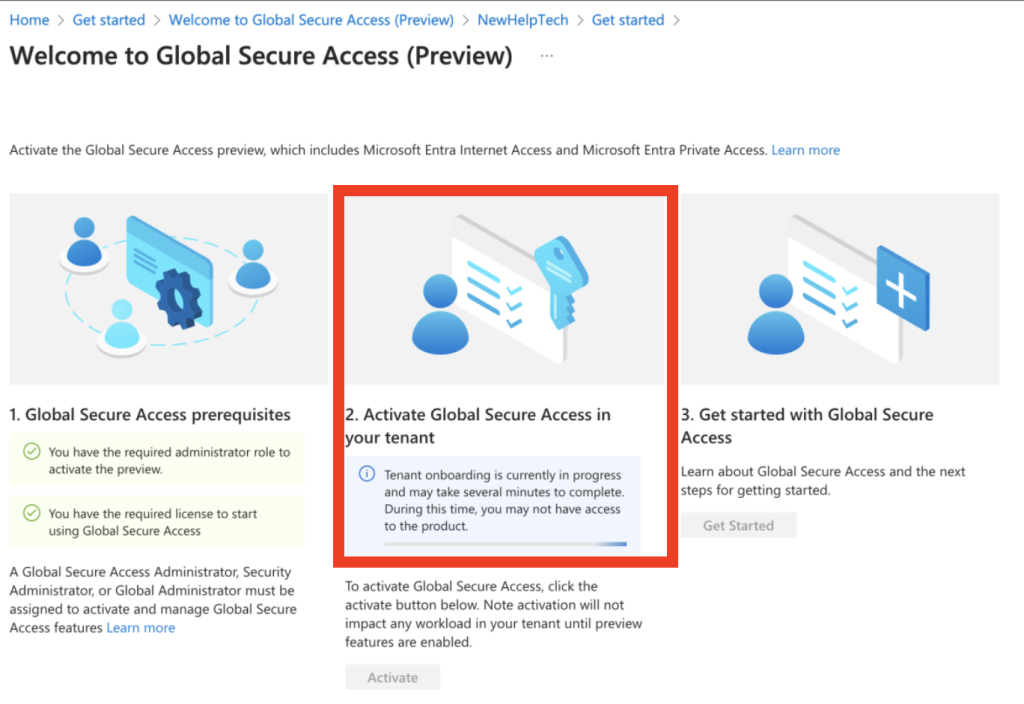
Step 3: Activate GSA for your tenant
- Click Activate GSA to enable the features for your tenant.
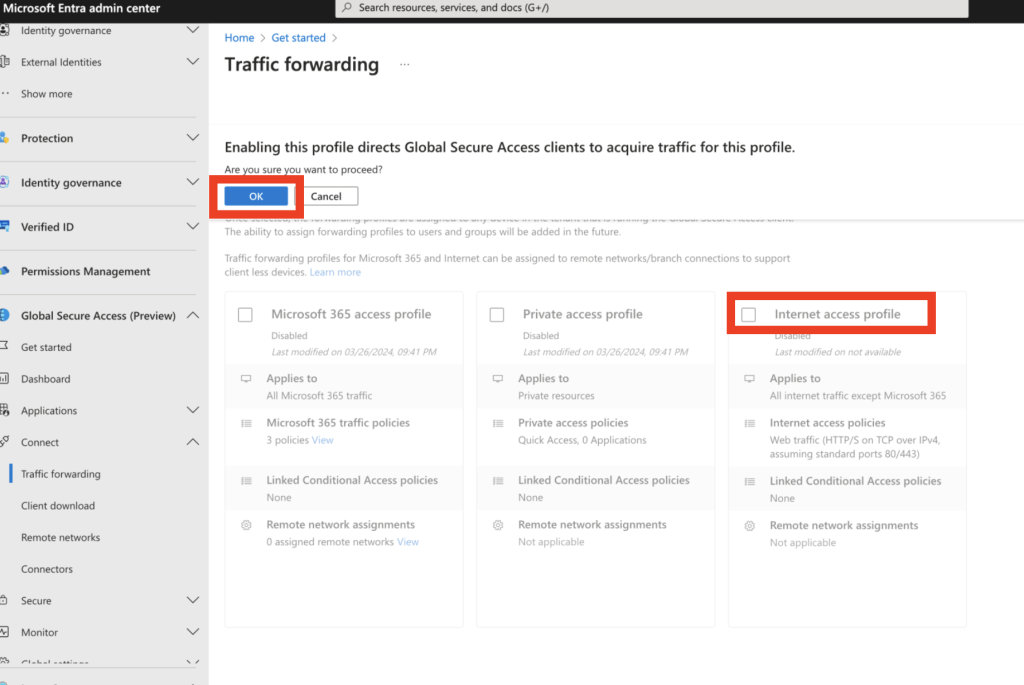
Step 4: Enable the Internet Access feature
- In the GSA Configuration section, go to the Connect tab and select Traffic Forwarding. Enable the Internet Access feature at the tenant level.
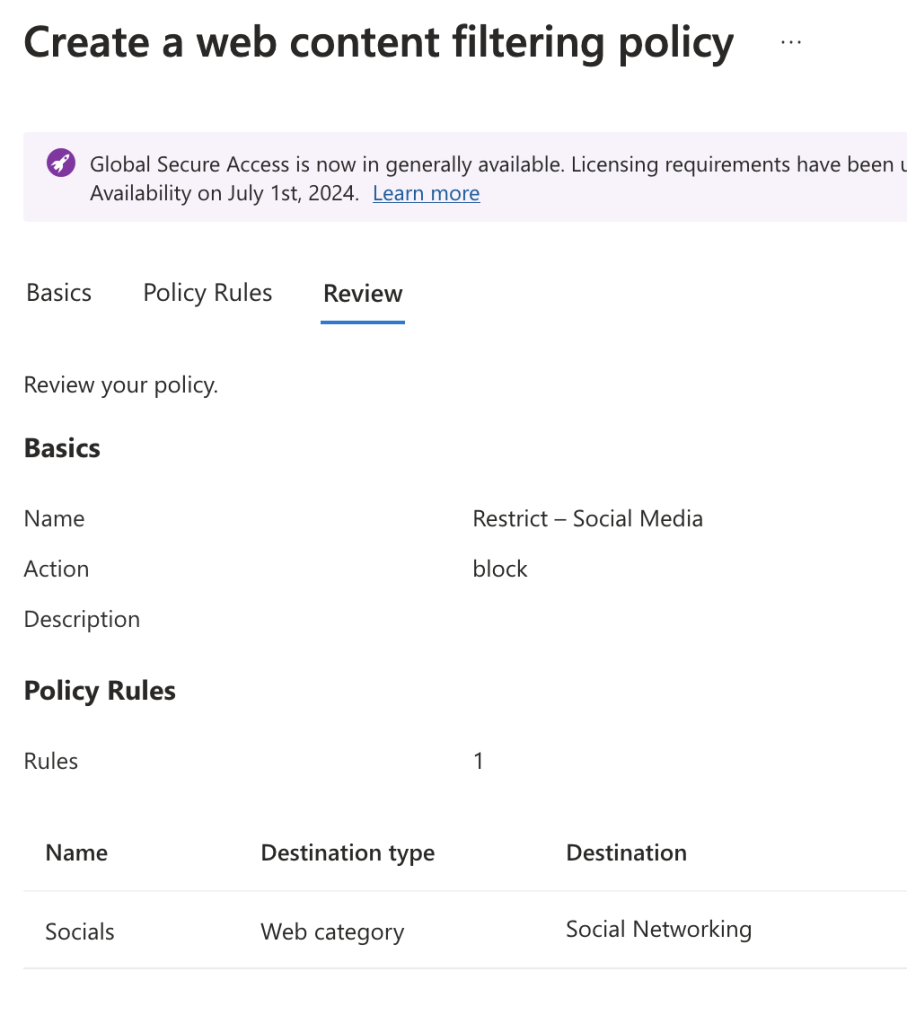
Step 5: Create Web Content Filtering Policies
- Go to Web Content Filtering policies under the Secure section. Create a policy by defining its name (e.g., “Restrict – Social Media”).
- Under the Policy Rules, select Add Rule and choose the relevant webCategory, such as “Social Networking”.
- Set the policy action to Block to restrict access to the selected content.
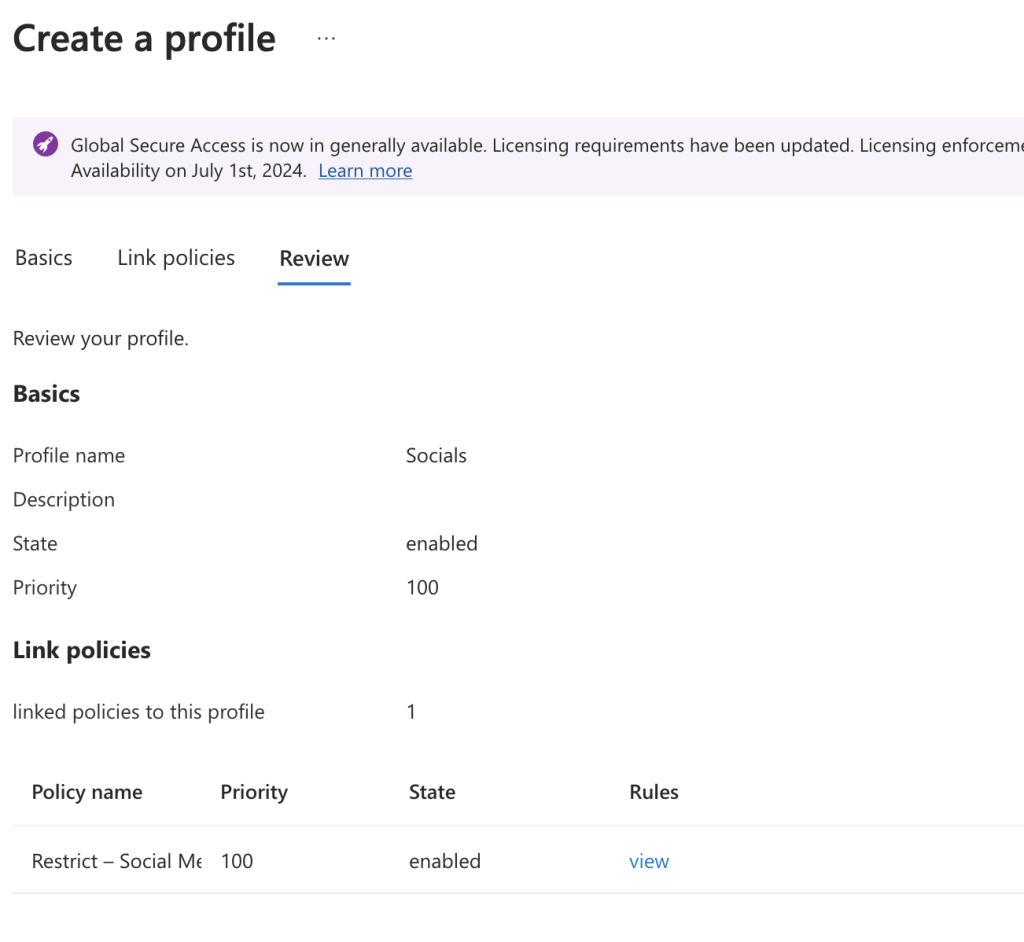
Step 6: Create Security Profiles
- In the Security Profiles section, click Create Profile to define a new profile. Ensure the profile is enabled and configure the priority.
- Link the Web Content Filtering policy you created earlier to this profile.
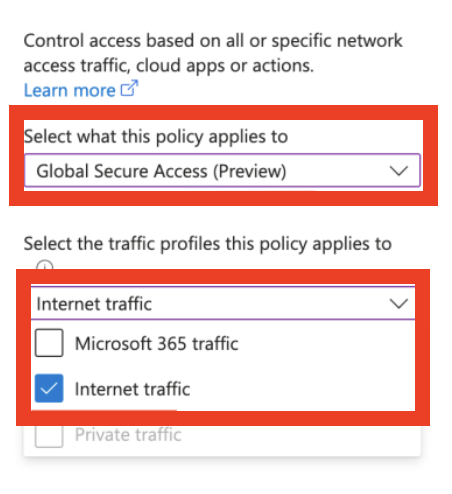
Step 7: Set up Conditional Access Policies
- Go to Conditional Access in the Protection section.
- Create a new policy, targeting the Target security group (for example). Choose the Global Secure Access resource and apply the appropriate Security Profile for that group.
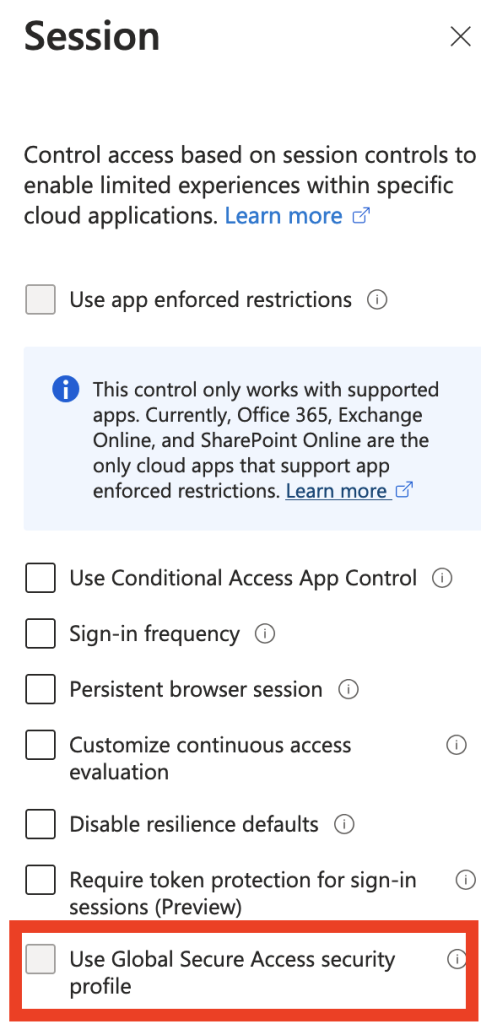
In the Session section:
- Find the option labeled “Use Global Secure Access security profile”.
- Select the security profile that should be deployed/scoped within this policy.
- After selecting the profile, click Select.
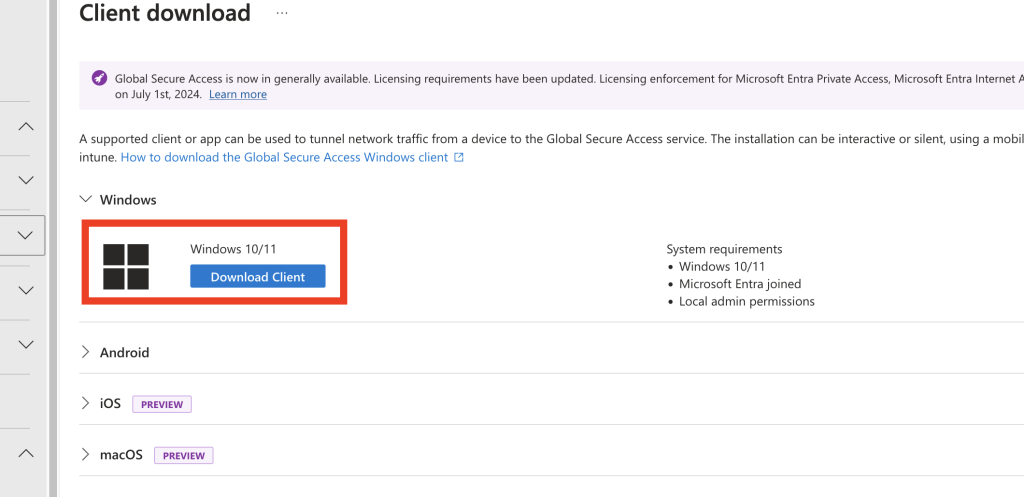
Step 8: Install the Global Secure Access Client
- Download and install the Global Secure Access client on your Entra-joined Windows device. After installation, log in with your M365 or Entra ID credentials.
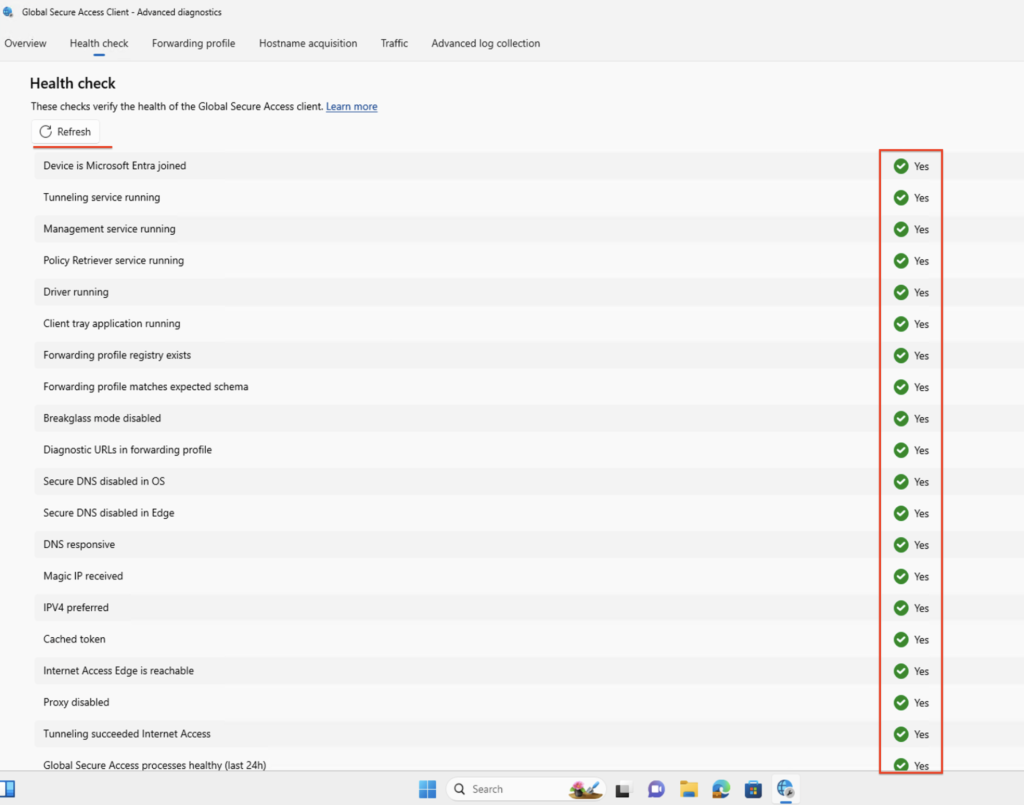
- Verify the connection by checking the Health Check in the client.
Step 9: Monitor Traffic and Logs
- Go to Traffic logs in the Entra portal to monitor traffic passing through the GSA solution. You can also export logs for further analysis.
Licensing Information
To use Microsoft Entra Global Secure Access, organisations must meet certain licensing requirements:
- Microsoft Entra ID P1: The core capabilities for Microsoft Entra Internet Access are now included in the Entra ID P1 license. This includes secure, fast, and consistent access to Microsoft services and seamless integration with Microsoft Entra Conditional Access.
Key features with Entra ID P1 include:
- Direct connectivity to Microsoft services, ensuring fast and resilient access to applications like Microsoft 365.
- Security and performance improvements with Compliant Network checks, enabling more effective control over network access.
- Conditional Access integration, which strengthens access controls for Microsoft services and apps.
- Enhanced visibility with improved activity logs and security event data for faster threat detection.
This update offers better value, helping organisations streamline security management while protecting users and data across Microsoft services.
Conclusion
Implementing Microsoft Entra Global Secure Access (GSA) with Internet Access is a powerful way to manage and secure web traffic across your organisation. By leveraging its integration with Microsoft Entra ID, you can enforce strict security policies, enhance user productivity, and protect sensitive data.
This guide has taken you through the steps required to successfully deploy GSA, from enabling the feature to configuring security profiles and monitoring traffic. Additionally, with the licensing update for Entra ID P1, GSA becomes a more accessible and valuable solution for organisations using Microsoft services.
As digital security continues to evolve, regularly reviewing and updating your configurations is essential to maintaining a secure and productive environment.

