Using a password manager? That’s a great start! However, managing passwords is just part of the equation. With stricter regulations like the NIS2 Directive (Network and Information Security Directive 2), organisations must take a more comprehensive approach to managing sensitive information, including usernames and passwords.
How can you ensure that credentials are controlled securely across your organisation while also meeting compliance standards? Microsoft Purview offers a robust set of tools to discover, classify, and manage credentials across your data estate—helping you reduce risks and achieve compliance with NIS2.
In this post, we’ll explore how to use Microsoft Purview for credential security and how it supports your journey towards NIS2 compliance.
Why Uncontrolled Credentials Are a Risk
Passwords improperly stored in spreadsheets or emails can lead to regulatory non-compliance and data breaches. NIS2 emphasises the need to protect essential services and infrastructure, meaning poor credential management can result in fines and reputational damage.
Real-World Use Case: Credential Detection and Remediation
A financial services company discovered that employees were storing service account credentials in shared spreadsheets. This posed significant risks both for security and compliance. Using Microsoft Purview’s scanning tools, the company identified these files and implemented automated DLP policies. Alerts notified administrators whenever credentials were detected in unauthorised locations. The files were temporarily blocked, allowing the team to secure them without disrupting operations. This proactive approach ensured compliance with NIS2 while reducing exposure to breaches.
Best Practices for Credential Security with Microsoft Purview
- Comprehensive Data Discovery
- Ensure complete visibility across all data sources—cloud, on-premises, and hybrid systems—to prevent storage gaps.
- Use scheduled scans to meet NIS2’s continuous monitoring requirements.
- https://learn.microsoft.com/en-us/purview/concept-scans-and-ingestion
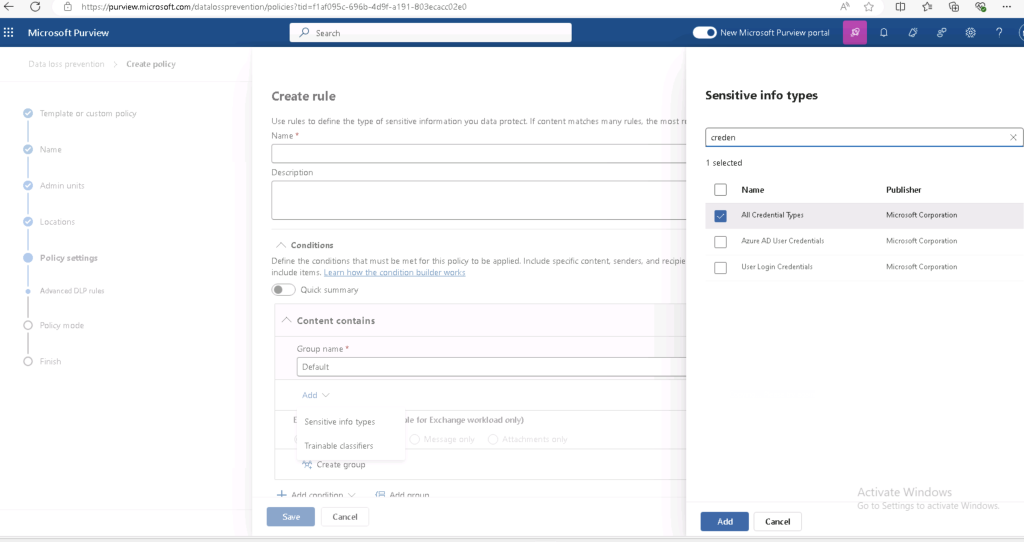
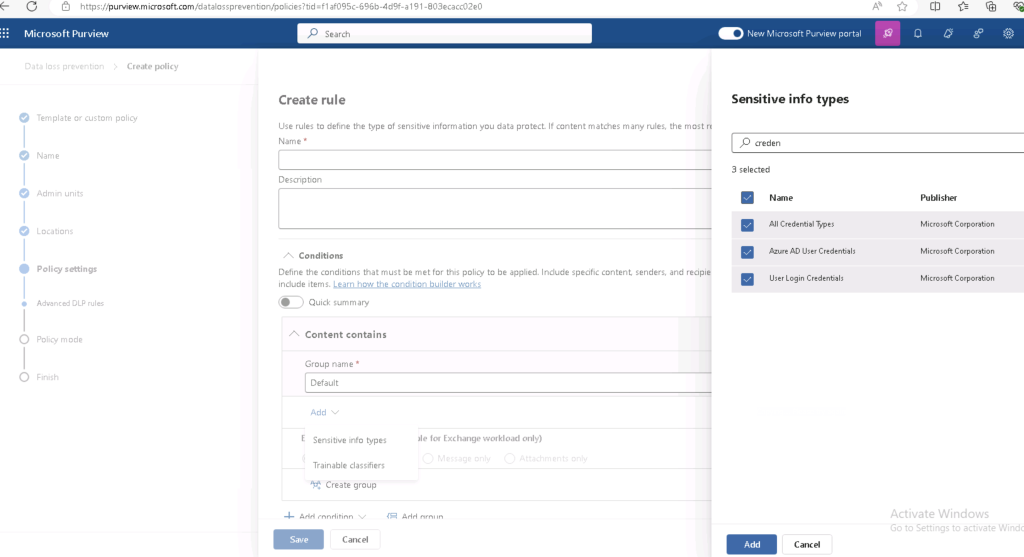
- Trainable Classifiers and Exact Data Matching (EDM)
- Use trainable classifiers to detect passwords hidden in complex documents.
- Deploy EDM classifiers to match credentials like usernames and passwords with precision.
- https://learn.microsoft.com/en-us/purview/trainable-classifiers-learn-about?view=o365-worldwide
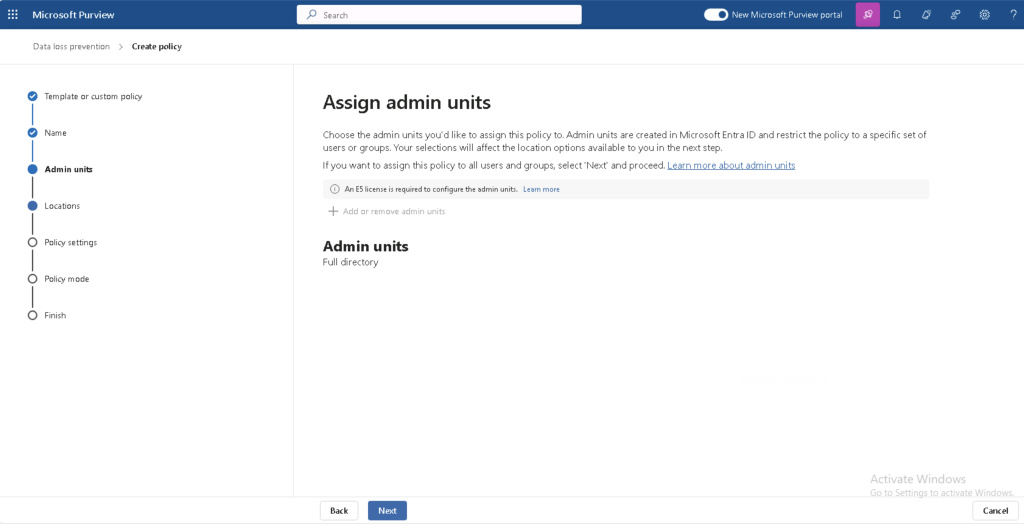
- Role-Based Access Controls (RBAC)
- Limit access to credentials by defining strict RBAC policies, ensuring only authorised personnel can access them.
- This aligns with NIS2’s emphasis on access control for sensitive data.
- https://learn.microsoft.com/en-us/purview/purview-compliance-portal-permissions
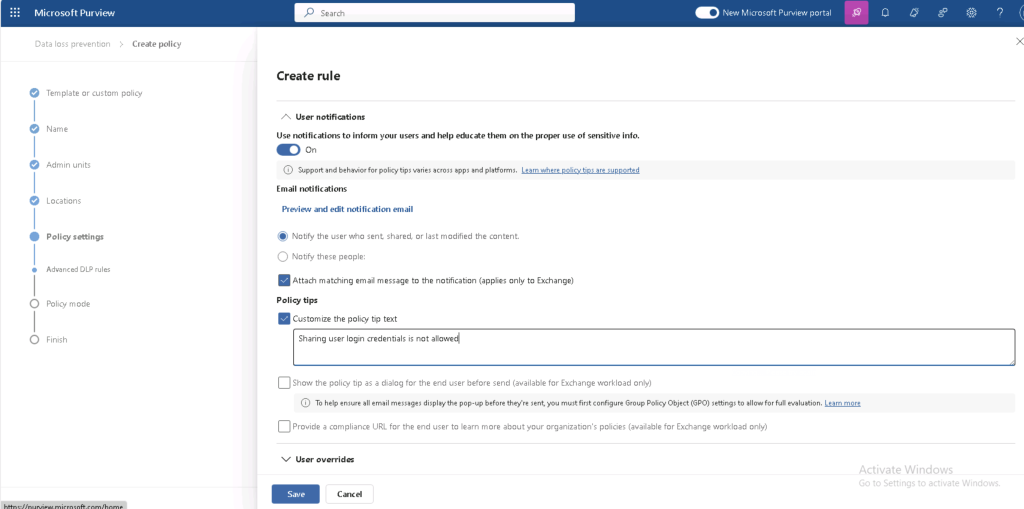
- Customise DLP Policies for Productivity
- Allow controlled sharing of credentials on company devices but restrict it on personal or public networks.
- Implement notification-only DLP policies to raise awareness without disrupting workflows.
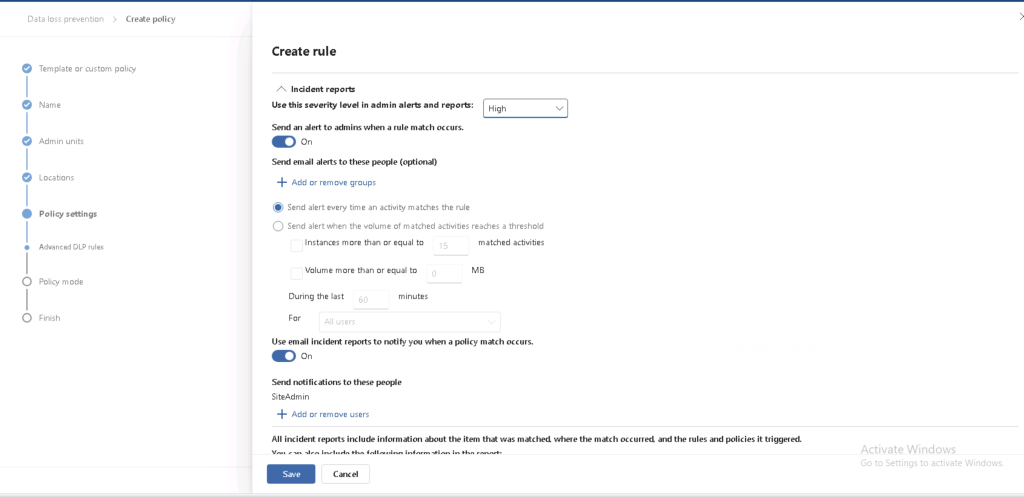
- Continuous Monitoring and Automated Remediation
- Set automated alerts for violations and implement automated actions like quarantining risky files.
- This ensures quick responses and helps maintain NIS2 compliance.
Step-by-Step: Implementing Credential DLP in Microsoft Purview
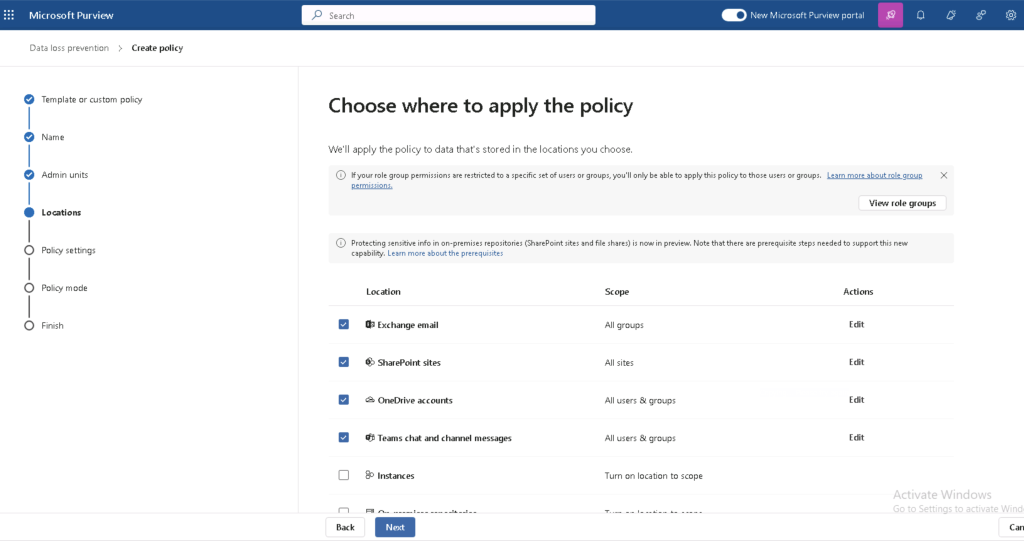
- Connect Data Sources
- Integrate on-premises, cloud, and hybrid environments to ensure full coverage for credential scanning.
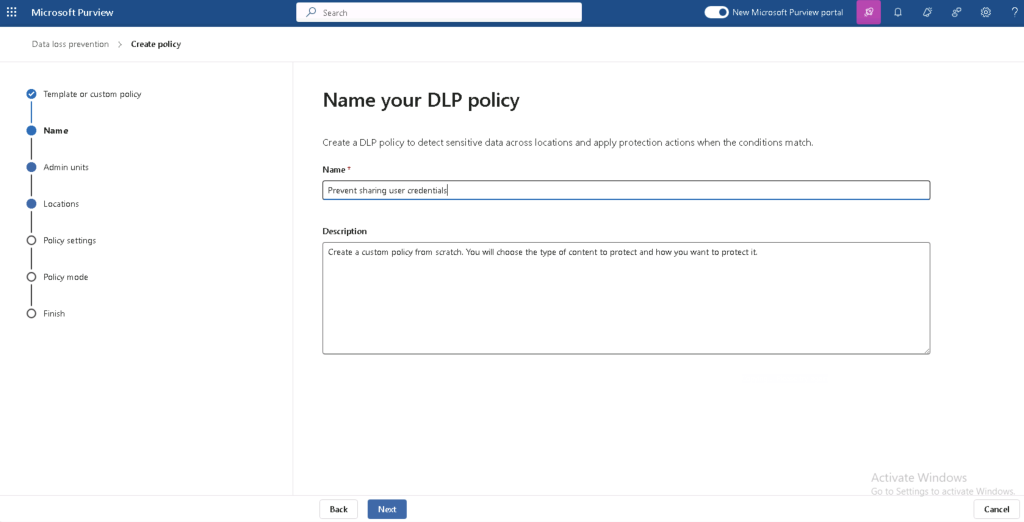
- Set Up Sensitivity Labels
- Create custom sensitivity labels for credentials (e.g., “Confidential – Passwords”).
- Apply these labels to emails, documents, and cloud apps to track usage.
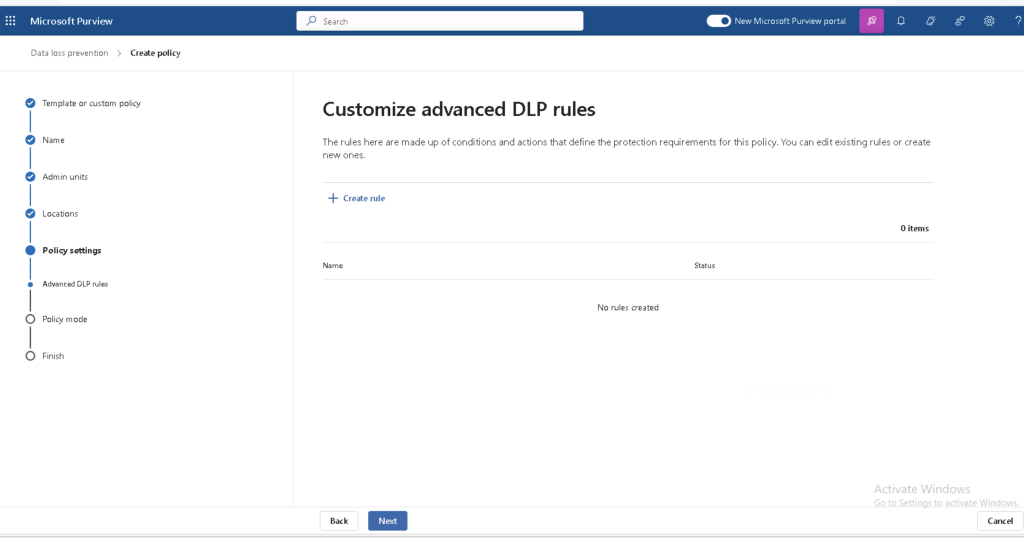
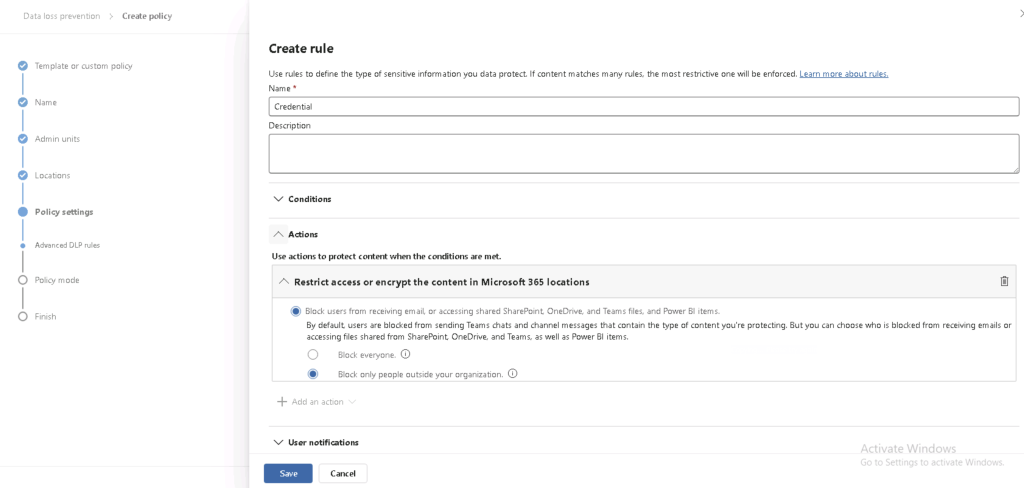
- Configure DLP Policies for Credentials
- Set DLP rules to restrict sharing of credentials via unauthorised channels.
- Use conditional access policies to allow usage on corporate-managed devices only.
- Review Advanced Configuration
- For EDM and endpoint DLP settings, explore the advanced tutorials on Microsoft Learn.
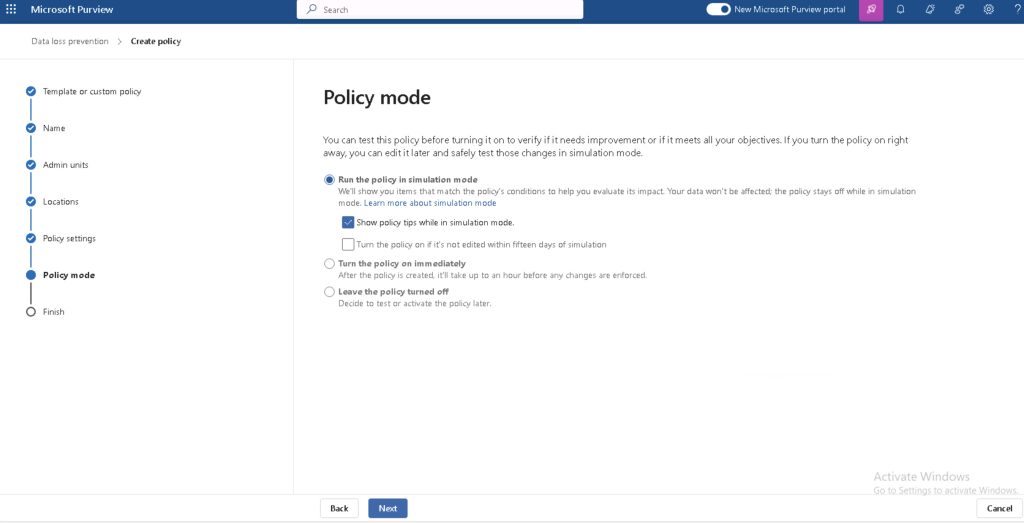
- Monitor, Alert, and Automate Actions
- Schedule regular scans and set alerts for policy violations.
- Automate actions such as quarantining sensitive files or blocking access when required.
Avoiding Licensing Pitfalls
Several advanced Purview features—such as DLP policies and EDM classifiers—require specific Microsoft 365 or Azure Purview licences.
- Microsoft 365 E5 Compliance Licence: Required for advanced DLP and automated sensitivity labelling.
- Azure Purview Subscription: Needed for data governance in multi-cloud and hybrid setups.
- Cost Planning: Ensure you evaluate your data volume to avoid unexpected costs.
Conclusion: Securing Credentials and Achieving NIS2 Compliance
Password managers alone are no longer sufficient for modern credential management. Microsoft Purview offers the tools needed for a comprehensive solution—providing visibility, control, and automation to meet NIS2’s demands.
By following best practices, customising DLP policies, and planning your licensing needs, your organisation can reduce security risks and protect critical infrastructure. With Microsoft Purview, you’ll have the tools to confidently manage sensitive credentials and maintain compliance in the digital era.

