Tag: Enterprise Security
-
Key Updates to OneDrive Retention Policies: What You Need to Know
Microsoft is updating OneDrive retention policies starting 27 January 2025, offering organisations more flexibility while addressing compliance needs and storage concerns. Learn what’s changing, why, and how to prepare
-

Strengthening Cloud Governance and Resilience with Microsoft
Effective cloud governance is critical in today’s digital landscape. Organisations must tackle risks, ensure compliance, and design resilient architectures to meet directives like NIS2. This guide outlines six essential steps to achieve robust cloud governance using Microsoft tools like Azure Service Health, Microsoft Defender for Cloud, and Azure Backup. From mitigating concentration risks to preparing…
-

Comprehensive Guide to Setting Up Microsoft Entra Global Secure Access (GSA) with Internet Access, Licensing, and Key Differences with SSE
Learn how to implement Microsoft Entra Global Secure Access (GSA) for secure internet access. This step-by-step guide covers everything from activating GSA for your tenant to configuring web content filtering, security profiles, and conditional access policies. Understand the key differences between GSA and Security Service Edge (SSE) and how to improve your organisation’s security posture.…
-

Introducing Enhanced File Integrity Monitoring (FIM) in Microsoft Defender for Cloud
Enhance your security with Microsoft Defender for Cloud’s improved File Integrity Monitoring (FIM). This powerful tool detects unauthorized changes to critical files and system configurations in real-time, ensuring compliance with regulations like NIS2 and PCI-DSS. Learn how FIM integrates with Microsoft Defender for Endpoint, provides real-time alerts, and helps safeguard your critical assets with proactive…
-

NIST Password Guidelines 2024: A Game Changer for Cybersecurity
**Excerpt:** Stay ahead in cybersecurity by adopting NIST’s updated password guidelines for 2024. The new **SP 800-63-4** emphasizes stronger password management, eliminating outdated practices like forced 60-day resets. Learn why passphrases, phish-resistant authentication, and dynamic password changes are the future of digital security. Make sure your systems, including Active Directory, are aligned with these modern…
-

Secure Your Intune Environment with Multi-Admin Approval: Everything You Need to Know
Multi-Admin Approval (MAA) is a security feature introduced in March 2023 in Microsoft Intune, enhancing security by requiring multiple admin approvals for high-risk actions. This powerful tool helps prevent unauthorised changes, reduces risks, and supports compliance. In this guide, we’ll explore how MAA works, its benefits, required licences, and provide a step-by-step tutorial on setting…
-

Entra ID Conditional Access Baseline
Every spring, as fresh interns arrive, they’re tasked with creating a Conditional Access baseline. While the concept may seem simple, these young minds continually surprise with innovative approaches to security, reminding us that building a robust foundation is an ever-evolving process.
-
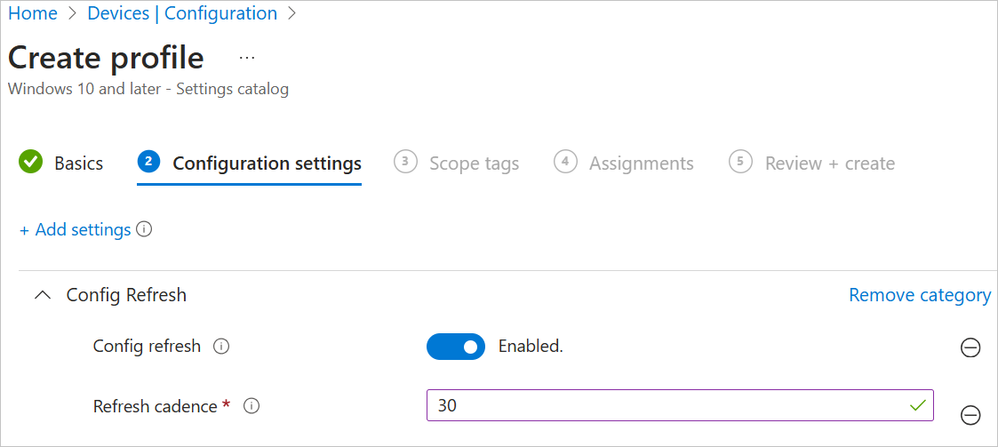
Simplify Device Compliance with Config Refresh: Essential for Endpoint Management
Discover how Microsoft’s new Config Refresh feature simplifies device compliance for systems and cloud engineers. This powerful MDM tool ensures consistent and secure configurations across your organisation, automatically correcting any deviations to maintain alignment with corporate policies. Integrating seamlessly with Microsoft Intune, Config Refresh is essential for effective endpoint management and reducing IT workload
-

Mastering NIS 2 Compliance with Microsoft Purview Compliance Manager
Mastering NIS 2 Compliance with Microsoft Purview Compliance Manager Navigating the complex requirements of NIS 2 compliance is crucial for CISOs. Microsoft Purview Compliance Manager offers a powerful tool to streamline and automate compliance within Microsoft 365. This guide explores how to use the platform to assess data protection risks, implement necessary controls, and stay…
-

Streamlining Security Operations with Microsoft Purview: A Role-Based Daily and Weekly Guide
Introduction So, you’ve just installed Microsoft Purview, and you’re probably wondering, “What’s next?” and “Who’s going to handle this?” Well, don’t worry; you’ve made a fantastic choice! Microsoft Purview is a brilliant data governance solution that helps your organisation classify, protect, and manage sensitive data across different platforms. But simply installing it isn’t enough; you’ve got…
