Tag: Compliance Management
-

Automate Your Onboarding and Offboarding in 15 Minutes with Entra Identity Governance
Onboarding and offboarding employees manually can lead to errors, delays, and compliance risks. With Microsoft Entra Identity Governance, you can automate these processes in just 15 minutes—no scripting required. Discover how to streamline user lifecycle management, enhance security, and maintain compliance with Entra’s powerful workflows and customisable extensions. Perfect for organisations looking to save time,…
-

Strengthening Cloud Governance and Resilience with Microsoft
Effective cloud governance is critical in today’s digital landscape. Organisations must tackle risks, ensure compliance, and design resilient architectures to meet directives like NIS2. This guide outlines six essential steps to achieve robust cloud governance using Microsoft tools like Azure Service Health, Microsoft Defender for Cloud, and Azure Backup. From mitigating concentration risks to preparing…
-
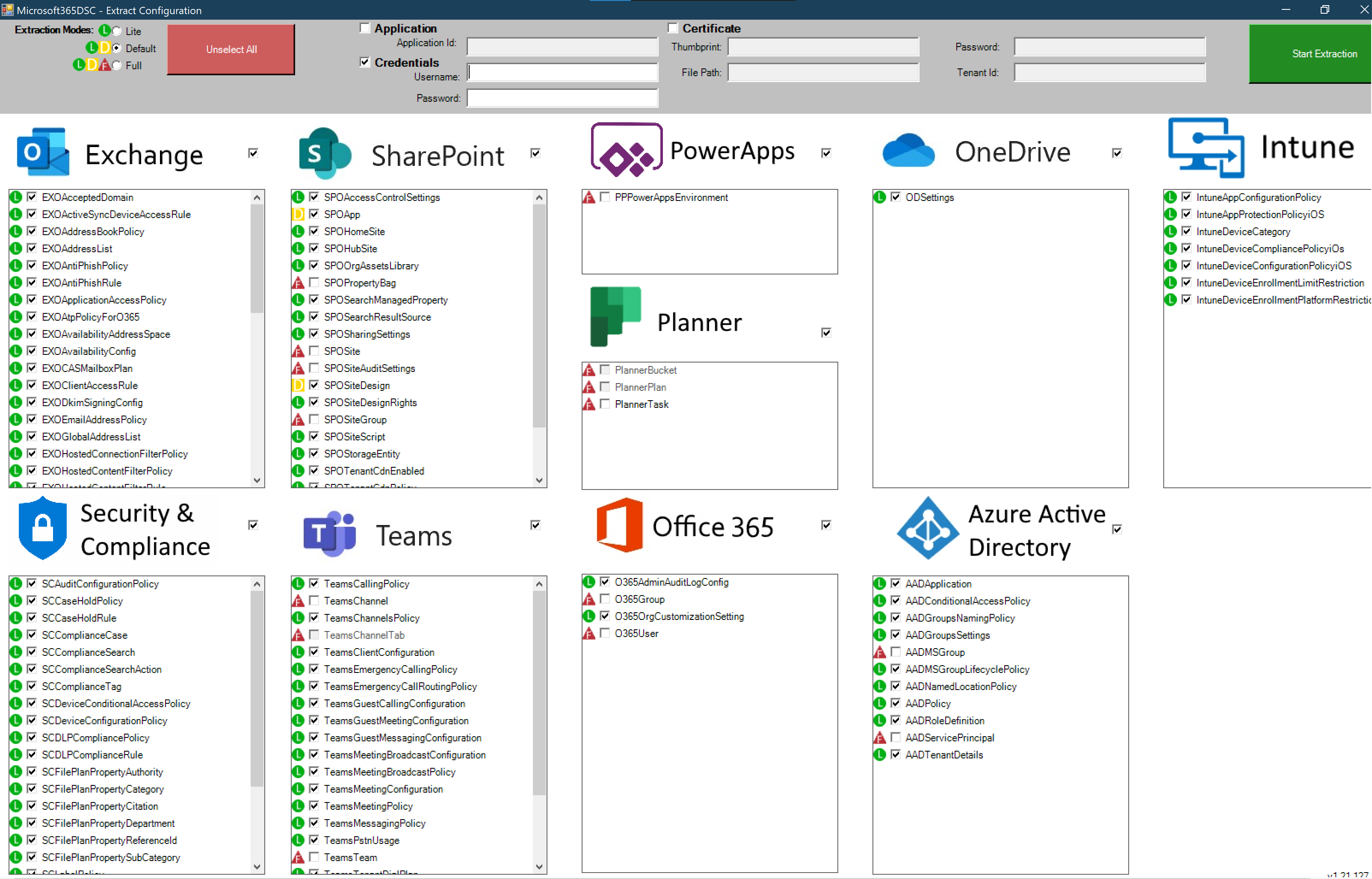
Microsoft 365 DSC: Automate, Configure, and Monitor Like a Pro
Discover how Microsoft 365 Desired State Configuration (DSC) empowers IT professionals to automate, monitor, and maintain tenant configurations with ease. This blog dives into the benefits of DSC, including drift prevention and multi-tenant synchronization, while providing a step-by-step guide for deployment. Learn from real-life examples covering Exchange Online, Intune, and Entra, and explore additional resources…
-

Managing Passwords in the Digital Age: Leveraging Microsoft Purview for Enhanced Credential Security and NIS2 Compliance
Are you using a password manager? That’s a great start, but credential management requires more than secure storage. With the NIS2 Directive imposing stricter cybersecurity standards, it’s essential to manage usernames and passwords with full visibility and compliance. Explore how Microsoft Purview enables advanced data scanning, automated remediation, and DLP policies to protect your credentials…
-

Introducing Enhanced File Integrity Monitoring (FIM) in Microsoft Defender for Cloud
Enhance your security with Microsoft Defender for Cloud’s improved File Integrity Monitoring (FIM). This powerful tool detects unauthorized changes to critical files and system configurations in real-time, ensuring compliance with regulations like NIS2 and PCI-DSS. Learn how FIM integrates with Microsoft Defender for Endpoint, provides real-time alerts, and helps safeguard your critical assets with proactive…
-

Unlocking DUDE: A Guide to Dynamic User and Device Enumeration
DUDE (Dynamic User and Device Enumeration) is a powerful tool for IT administrators to automate the process of retrieving and managing user and device data from Azure AD. Leveraging Microsoft Graph API and PowerShell, DUDE streamlines security monitoring, compliance reporting, and device management. This guide covers its architecture, setup, common use cases, and real-world applications…
-

Secure Your Intune Environment with Multi-Admin Approval: Everything You Need to Know
Multi-Admin Approval (MAA) is a security feature introduced in March 2023 in Microsoft Intune, enhancing security by requiring multiple admin approvals for high-risk actions. This powerful tool helps prevent unauthorised changes, reduces risks, and supports compliance. In this guide, we’ll explore how MAA works, its benefits, required licences, and provide a step-by-step tutorial on setting…
-

Understanding the Differences Between Intune Update Rings and Windows Autopatch
Managing Windows updates can be challenging, but choosing the right tool is crucial. This post explores the differences between Intune Update Rings and Intune Windows Autopatch, two powerful Microsoft solutions that cater to different IT management needs. Discover which option offers the best balance of control and automation for your organisation.
-
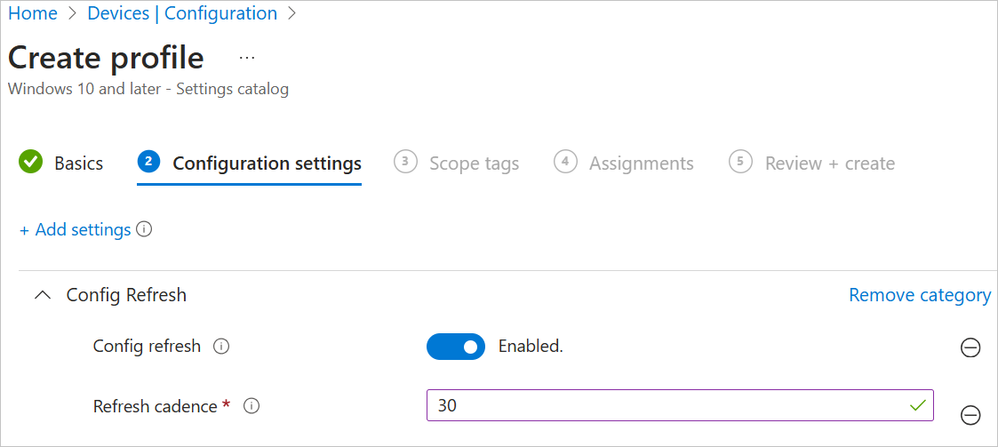
Simplify Device Compliance with Config Refresh: Essential for Endpoint Management
Discover how Microsoft’s new Config Refresh feature simplifies device compliance for systems and cloud engineers. This powerful MDM tool ensures consistent and secure configurations across your organisation, automatically correcting any deviations to maintain alignment with corporate policies. Integrating seamlessly with Microsoft Intune, Config Refresh is essential for effective endpoint management and reducing IT workload
-

Mastering NIS 2 Compliance with Microsoft Purview Compliance Manager
Mastering NIS 2 Compliance with Microsoft Purview Compliance Manager Navigating the complex requirements of NIS 2 compliance is crucial for CISOs. Microsoft Purview Compliance Manager offers a powerful tool to streamline and automate compliance within Microsoft 365. This guide explores how to use the platform to assess data protection risks, implement necessary controls, and stay…
