Category: General
-

Strengthening Cloud Governance and Resilience with Microsoft
Effective cloud governance is critical in today’s digital landscape. Organisations must tackle risks, ensure compliance, and design resilient architectures to meet directives like NIS2. This guide outlines six essential steps to achieve robust cloud governance using Microsoft tools like Azure Service Health, Microsoft Defender for Cloud, and Azure Backup. From mitigating concentration risks to preparing…
-

Why Password Policies Matter and How Often to Update Them
In today’s digital age, securing online accounts goes beyond just choosing a strong password. Frequent password changes, once seen as a key security measure, may actually do more harm than good. This blog explores the latest insights from NIST and Microsoft, highlighting why password policies should focus on long, complex passwords and multi-factor authentication (MFA)…
-
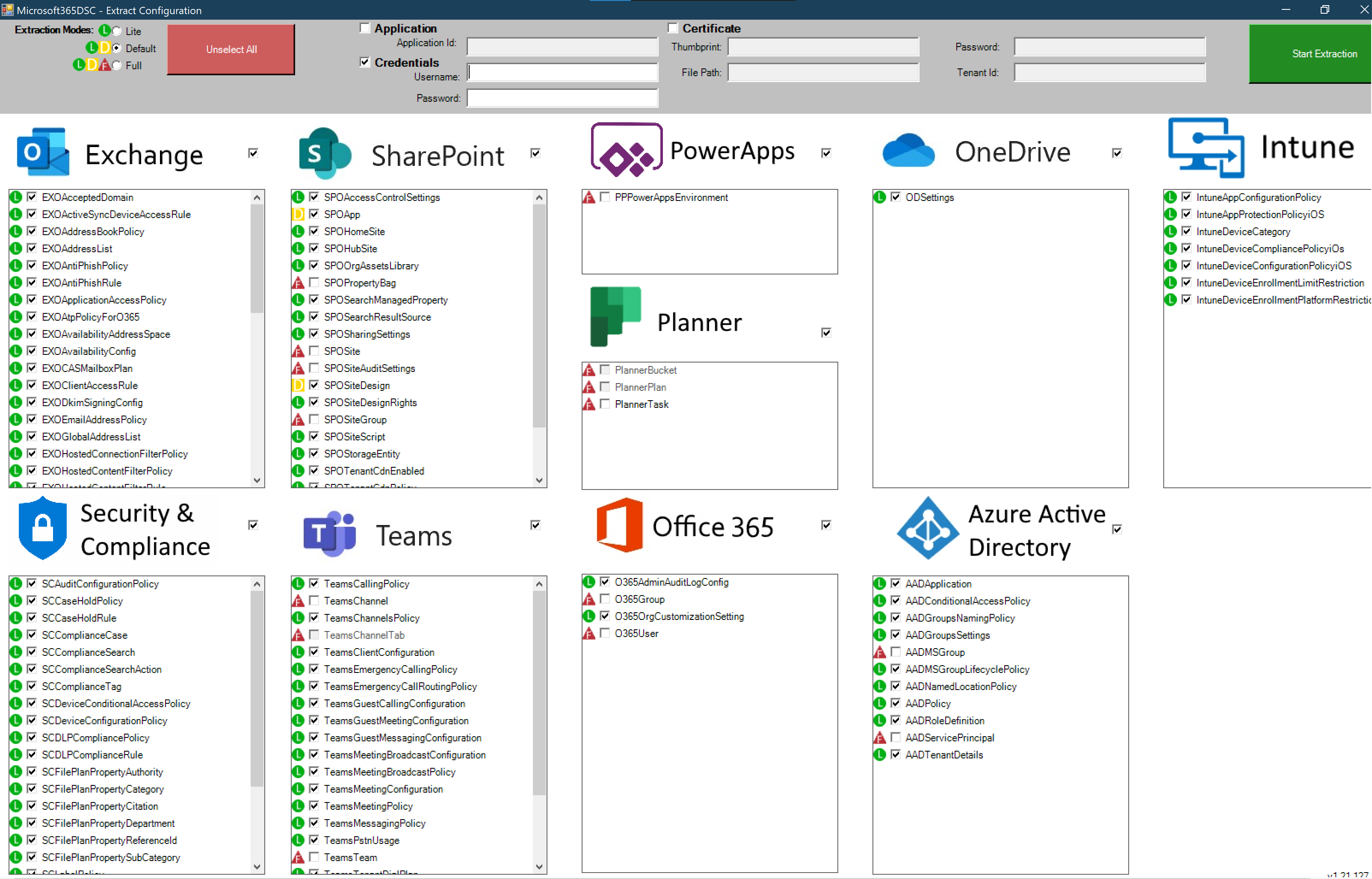
Microsoft 365 DSC: Automate, Configure, and Monitor Like a Pro
Discover how Microsoft 365 Desired State Configuration (DSC) empowers IT professionals to automate, monitor, and maintain tenant configurations with ease. This blog dives into the benefits of DSC, including drift prevention and multi-tenant synchronization, while providing a step-by-step guide for deployment. Learn from real-life examples covering Exchange Online, Intune, and Entra, and explore additional resources…
-

Introducing Enhanced File Integrity Monitoring (FIM) in Microsoft Defender for Cloud
Enhance your security with Microsoft Defender for Cloud’s improved File Integrity Monitoring (FIM). This powerful tool detects unauthorized changes to critical files and system configurations in real-time, ensuring compliance with regulations like NIS2 and PCI-DSS. Learn how FIM integrates with Microsoft Defender for Endpoint, provides real-time alerts, and helps safeguard your critical assets with proactive…
-

NIST Password Guidelines 2024: A Game Changer for Cybersecurity
**Excerpt:** Stay ahead in cybersecurity by adopting NIST’s updated password guidelines for 2024. The new **SP 800-63-4** emphasizes stronger password management, eliminating outdated practices like forced 60-day resets. Learn why passphrases, phish-resistant authentication, and dynamic password changes are the future of digital security. Make sure your systems, including Active Directory, are aligned with these modern…
-

Unlocking DUDE: A Guide to Dynamic User and Device Enumeration
DUDE (Dynamic User and Device Enumeration) is a powerful tool for IT administrators to automate the process of retrieving and managing user and device data from Azure AD. Leveraging Microsoft Graph API and PowerShell, DUDE streamlines security monitoring, compliance reporting, and device management. This guide covers its architecture, setup, common use cases, and real-world applications…
-

Hello world! I’m Back After 15 Years.
Hello, world! It’s been a long time, and I’m thrilled to be back in the blogging sphere after a 15-year hiatus. A lot has changed since I last typed away my thoughts on my old blog, where I delved into the intricate realms of technology, personal insights, and everything in between. This time around, I’m excited…
